By Elizabeth Hall
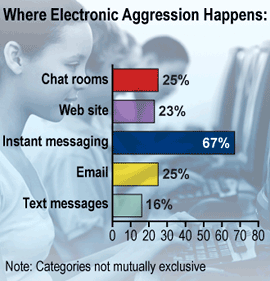 |
| English: A graph showing where electronic aggression occurs. (Photo credit: Wikipedia) |
Introduction
These days, computers are everywhere, and most of us carry them with us in the form of Smartphones, tablets, and notebooks everywhere we go (Evans, Martin & Poatsey, 2011). While at first glance this seems wonderful, and makes it possible for us to be connected and share our lives with family and friends or even work on the go, when looking closely it also provides criminals with easier access to us. This means that our personal information, along with an anonymous platform where it is easier to say what we think without repercussion is available to everyone whether he or she has scruples or not. This leaves us more open to several different types of crimes that were harder to accomplish before the introduction to computers in mainstream society (Evans, Martin & Poatsey, 2011). In this essay, we will define what these crimes are the differences in them, and ways to protect yourself from them.
Difference in Harassment, Threats, and Cyberstalking
 |
| English: http://noalciberacoso.blogspot.com/ Español: http://noalciberacoso.blogspot.com/ (Photo credit: Wikipedia) |
Three of the crimes that we will discuss are harassment, threats, and Cyberstalking. Harassment, according to Knetzger, & Muraski (2008), is when someone continues to try to communicate and interact with someone else specifically with the goal of intimidation, emotional upset, or annoyance to the victim. Threats are communications that imply some negative connotation of physical or mental harm that the person making the threat intends to carry out. A person who threatens harm or ha
rasses someone by means of the Internet, or any other electronic forms of media defines Cyberstalking, and is a Class B misdemeanor if caught. As we know, harassment and threatening are crimes, so why should it be different electronically?
| English: An example of cyber-bullying on gmail chat (Photo credit: Wikipedia) |
Difference in Cyberstalking and Cyber Bullying
There is another term we may hear often, cyber bullying. This is not to be mistaken with Cyberstalking because it is somewhat different as noted by Knetzger, & Muraski (2008). Cyber bullying is also somewhat the same as cyber stalking; the difference is that the criminals and victims are all minors. Both of these crimes are prosecuted under similar legislation and laws, however one is prosecuted in juvenile court, and the other is prosecuted in adult court systems. These crimes can be committed by email, SMS, or Instant Messaging (IM) and can often be more intense than cases of physical stalking or harassment or threats because of the ease and anonymity assumed by people using electronic devices (Knetzger, & Muraski, 2008).
Defining Identity Theft
 |
| D'Press 07 Jan 2009 (Photo credit: kishorebudha) |
Strain (n.d.) holds that identity theft means a criminal acquires someone else’s personal information, with the intent to use it to commit a crime such as fraud, theft, to avoid detection. Usually the person whose identity has been stolen does not find out about it until later when they themselves are applying for a loan, mortgage, or credit card. Some thieves, as in the case of Albert Gonzalez, who led a transnational ring of identity thieves and managed to steal forty million different credit and debit cardholder’s information, manage to get large amounts of information from unsuspecting people while working as a police informant (Feeley, & Van Voris, 2010). The three types of identity theft are true name fraud, account take over and criminal identity theft (Knetzger, & Muraski, 2008). There are several ways that these thieves can obtain your information so be vigilant when we discuss five of t
he more common ways that you may be getting deceived and you might avoid becoming a victim.
 |
| muraski waiting (Photo credit: rocketjim54) |
Five Common Ways Thieves Obtain Your Information
There are numerous ways that thieves can obtain your personal information discussed by Knetzger, & Muraski (2008). We will discuss five of them here and tell you if there are any ways to protect yourself from them. The first way as in the case of Mr. Gonzalez, is for them to hack into computers that hold the information and steal it in large quantities. They usually hack into a business that has the information electronically and copy it. Another way that they obtain the information is by dumpster diving, and it is what it sounds like, thieves stealing your trash and sorting through it. You can protect yourself by shredding your junk mail, receipts, and documents before disposing of them (Knetzger, & Muraski, 2008).
 |
| WASHINGTON - JULY 25: U.S. Attorney General Eric Holder (L) passes Secretary of Homeland Security Janet Napolitano (R) during the unveiling of a new strategy to combat Transnational Organized Crime (TOC) at the South Court Auditorium at the Eisenhower Executive Office Building July 25, 2011 in Washington, DC. The initiative gives the government a widened framework when dealing with transnational organized crime and also an provides an invitation for enhanced international cooperation. (Image credit: Getty Images via @daylife) |
The third method we will talk about is outright stealing it from your mailboxes, cars, or homes (Knetzger, & Muraski, 2008). You can protect yourself from this crime somewhat by not leaving personal information in your car, and by getting a mailbox with a key or a post office box. Yet another method that is avoidable is the shoulder surfing method when a thief watches over your shoulder when entering personal information, and gets the information in plain sight. The last common method here is through email and web site scams, in which you might be offered free products (pay shipping only), or employment so you type your information in, and they have it. This is known as phishing and is very common on the internet and in emails.
What is a 4-1-9 Scam?
Knetzger, & Muraski (2008) notes that a 4-1-9 scam is also known as an advanced fee scam, and is known by the 4-1-9 for the area that it dominates from which is Nigeria and the Penal Codes associated with the fraud. They also hold that 90% of these crimes happen under the fund transfer scheme. How this works is someone from Nigeria or claiming to be Nigerian sends out mass emails claiming to be some sort of dignitary or customs official. These emails usually involve wills, trust funds, etc., and claim that the person needs someone in the United States to help with the transfer of the funds associated with the will, or trust fund. In return for helping, the email recipient will receive a portion of the money, which is usually listed in the millions. All they have to do is send some money to ascertain the release of the sum. The victim sends the money to receive nothing, or a communication stating that more money is needed to complete the transfer. Most of these will have many grammatical errors, and will ask for personal information as well as the fees.
Conclusion
 |
| Five ways to fight sexual harassment(public service poster on a Seoul Subway Line 2 train) (Photo credit: Wikipedia) |
In today’s modern world, computers are important to almost everything we as consumers do, whether that means work or recreation. We pull out our smart phones and look up our locations as related to our favorite places, shopping, family friends, and almost everyone has one. On the surface, this makes our data, family, work, and friends accessible, and possibly our lives easier however we must be vigilant because the criminal elements have them as well. This has also brought us to an era of crimes that spans the entire world, and is available at our fingertips wherever we go, Cyberstalking, cyber bullying, identity theft, and other ways to use computers for crime open up a new avenue for law enforcement to patrol.
References:
Banerjee, A., Barman D., & Bhuyan, L.N., (n.d.). Cyber-Fraud is One Typo Away. Department of Computer Science and Engineering. University of California, Riverside. Retrieved From: http://www.citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.163.3828...
Evans, A. Martin, K. & Poatsey, M.A., (2011). Technology in Action (7thEd.) Upper Saddle River, NJ: Pearson/Prentice Hall. ISBN 10: 0-13-509669-3
Feeley, J. & Van Voris, B., (2010). Hacker Gets 20 years in Largest Identity Theft Case (Update 2). Retrieved From: http://www.bloomberg.com/apps/news?pid=newsarchive&sid=aCDo3co5A0Zk
Knetzger, M. and Muraski, J. (2008) Investigating high-tech crime (1st Ed.). Upper Saddle River, NJ: Pearson/Prentice Hall. ISBN eBook: 0536085773
Strain, P., (n.d.). Phishing Don’t Phall for it. Part 1. Retrieved From: http://www.uakron.edu/dotAsset/2195277.pdf


















0 comments:
Post a Comment